
What is Database Security | Database Security Threats
A decent measure of vital corporate data dwells in Database advances.
Besides client data they likewise contain private data that can definitively affect a business.
It is must for every individual to find answers for the question of what is database security to ensure a smooth flow of functionality
Be that as it may, not very numerous organizations are as genuine towards the security of the database innovations as they ought to be.
A proactive approach towards protecting them from programmers and malignant components alongside continually distinguishing and establishing an escape route is required.
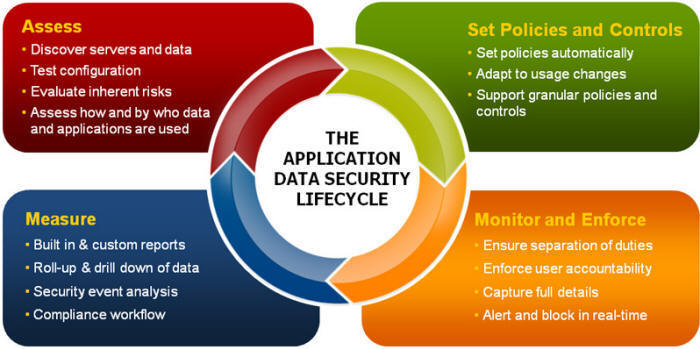
How to deal with database security issues
Various organizations are finding a way to enhance their security position and better guard your data.
2018 has seen organizations like Panera Bread, Facebook, and Uber getting involved in noteworthy data breach revelations.
In the event that you communicate with any of these fat cats on the web, odds are you’re a casualty.
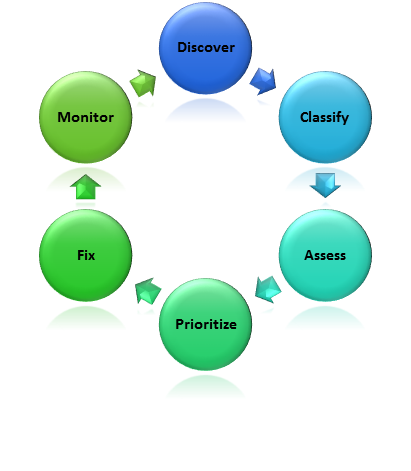
Let’s take a look at the Database Security Lifecycle
Top five hints to assess the database security threats and patch them
- What type of database are you using
- Have 100% detectable access to data
- Focus on important database resources
- Keep track of the premium user’s activity
- How about having Machine Learning on board?
- What type of database are you using
- What type of Database are you using?
Your security planning relies on the kind of database server you are utilizing.
For instance, MSSQL accompanies default approval framework while you have to introduce extra modules if you are working with MYSQL.
Guaranteeing the total security at the crucial level is imperative.
Make it obligatory to enter an intense solid secret key while you make the client account.
For the best outcomes, you have to make an approach that requires a base length, no less than one unique character and a blend of capitalized/lowercase letters.
- Have 100% detectable access to data
As simple as this, we can’t safeguard what we can’t see.
It is always preferred to examine and seize the entire database access for auditing reasons.
However, the catch here is that having local auditing systems on most database frameworks will bring about a downfall in their performance.
To beat this, consider approaching a third party database review and assurance arrangement which does not require local evaluation to be empowered but would still furnish you with 100% data get to permeability.
- Focus on Important database resources
Pay heed to essential database resources, identified using Business Impact Analysis.
It is highly challenging to wrap the threat that looms around each asset.
Even the largest of companies, with access to all kinds of tools and technologies, find it difficult to get a hold of these threats.
The whole concentration should be on the critical assets, which, if compromised, would have a huge cynical impression on the organization.
Hence it is always a smart move to have the BIA done in advance to identify the critical assets which need to be focused upon.
- Keep track of the premium user’s activity
Premium Clients have privileged rights to the data of the application.
Observing the pattern of their activities could let us know if any kind of unauthorized activities, inquiring the data, is happening or not.
It will help us identify if any sort of sensitive data is being compromised at the user level.
Also, if the data is being compromised then what was the data used for?
- How about having Machine Learning on board?
Machine learning, without human impedance, can gather, break down, and process information.
It is designed in such a manner that it would examine any past digital assault.
Based on the nature of the attack it builds an understanding and creates a firewall accordingly.
This approach empowers an automated digital barrier framework with very little security personnel.
For instance, Webshell. It is a chunk of code which is perniciously stuffed inside a site with a specific end goal.
It helps to enable the assailant to influence alterations on the web root directory of the server.
This implies that the assailant gains full access to the database of the application.
In the case of a business having an e-commerce site, the assailants may get to the database consistently with a specific end goal to gather credit or debit card data of the clients.

How could Machine Learning aid us in statistical database security?
Study the behavior of an ordinary shopping basket and record the data.
This data can be utilized to tutor the machine learning prototype to differentiate between a usual behavior and a vindictive one.
Detected corrupt files can be executed on a guarded solitary system to coach the prototype additionally.
Hence, Machine Learning algorithms can be utilized to recognize web shells and segregate them from the application before they misuse the application.
Database Security Tutorial
Database security issues and how to avoid them
A database security director is the most essential resource for keeping up and anchoring touchy information inside an association.
Database security directors are required to perform various tasks and juggle an assortment of cerebral pains that go with the support of a protected database.
Everyday Maintenance
Database review logs require constant auditing to verify that there has been no information abuse.
Changed Security Methods for Applications
More often than not application engineers fluctuate the strategies for security for various applications.
Applications are being used inside the database.
This can cause trouble while making approaches for getting into the application.
The database should likewise have the best possible access controls. Controls for directing the fluctuating techniques of hackers, to secure the sensitive information from getting leaked.
Application Spoofing
Hackers are fit for replicating applications that look like the original applications in association with the database.
These unapproved applications are frequently hard to recognize.
It also permit programmers to access the database by means of masking the application.
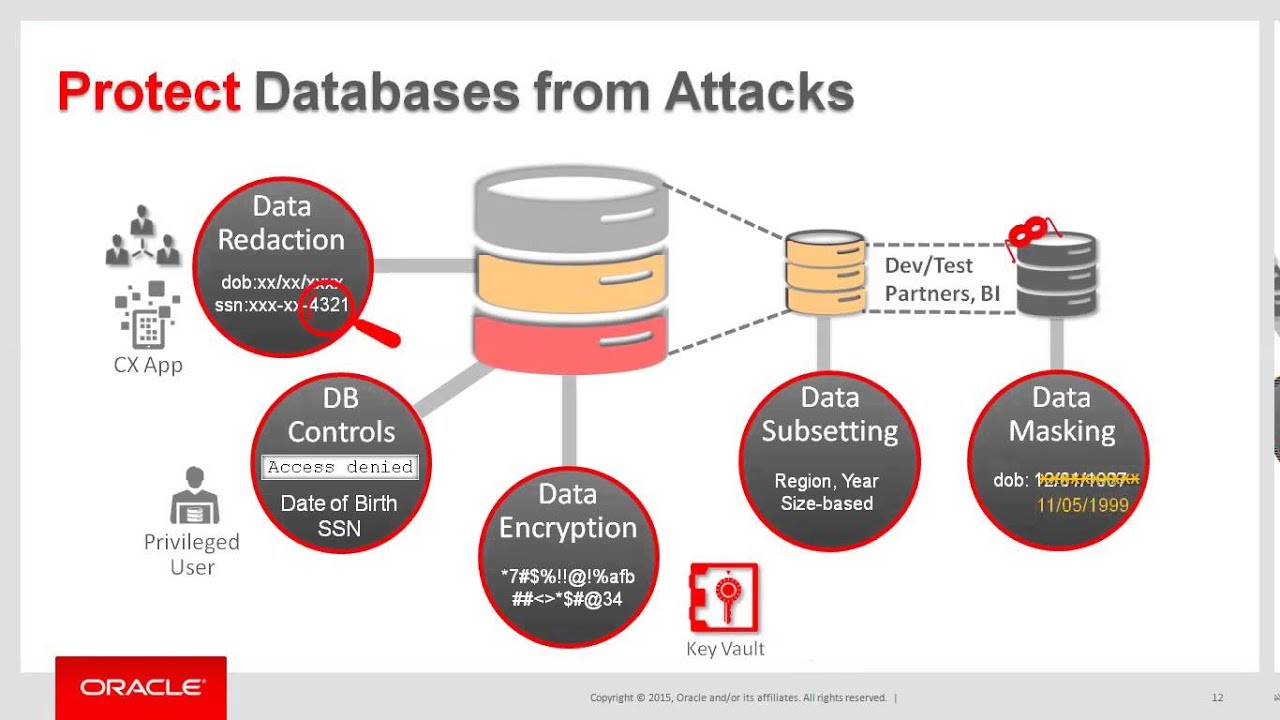
Conclusion
It is highly suggested for every company or an organization to take up security seriously because of various reasons.
Teknotrait is one of the reputed companies, which is dealing with various kinds of services related to testing, web development, digital marketing, app development and so on.
We are offering a free consultation for organizations, which helps them to find out any kind of security issues in the system.
Connect with us to enjoy



Pingback: Awareness on Phishing Emails and their Identification | Teknottrait Solutions- Blog